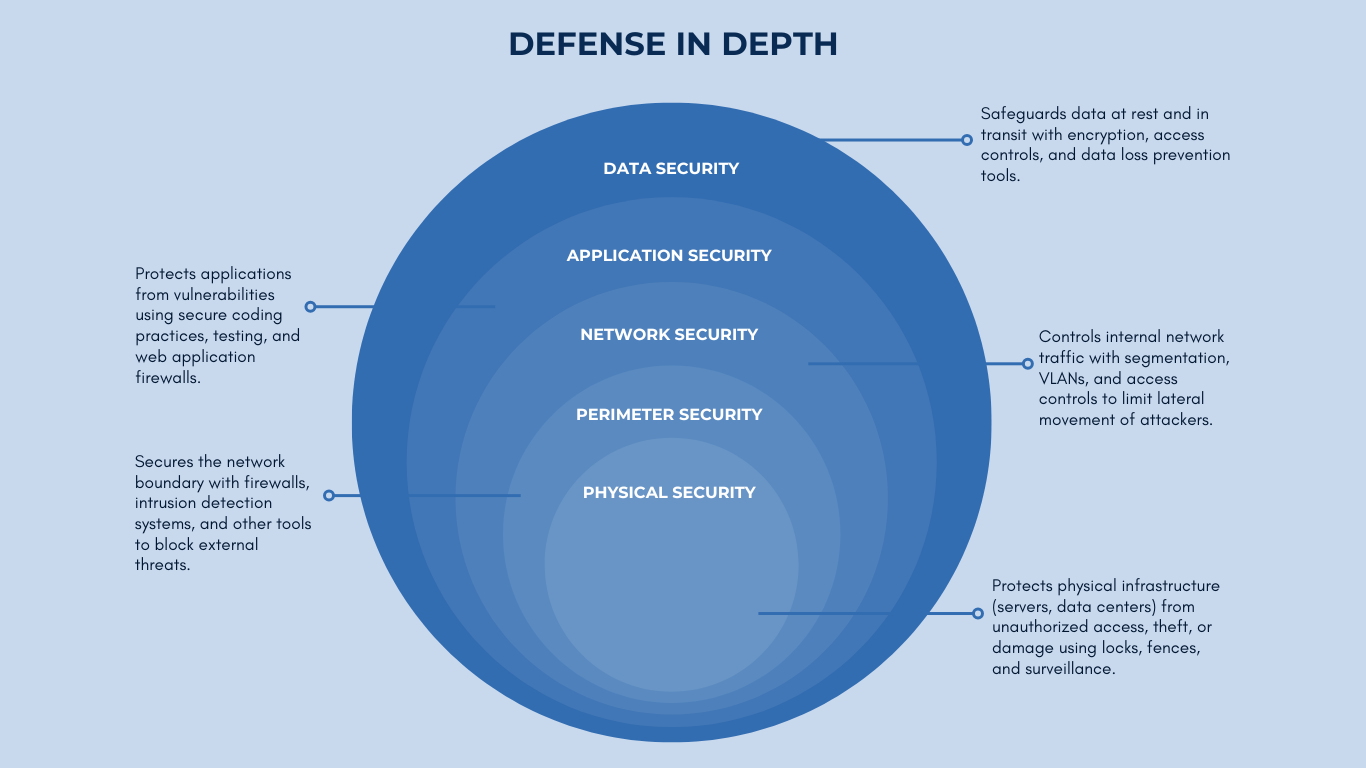
Cloud & Data Security
At Agiletek CYBER, we provide cutting-edge Cloud & Data Security solutions to protect your sensitive information and ensure secure cloud operations. Whether you operate in a hybrid, multi-cloud, or fully cloud-based environment, our strategies help mitigate risks and maintain compliance.
Cloud Security Architecture
Implement zero-trust frameworks, encryption, and access controls to safeguard your cloud infrastructure.
Data Protection & Encryption
Secure critical data at rest, in transit, and in use with advanced encryption and tokenization techniques.
Threat Detection & Incident Response
Leverage AI-driven monitoring and automated threat detection to identify and neutralize cyber threats in real time.
Compliance & Risk Management
Ensure compliance with GDPR, HIPAA, ISO 27001, and other industry regulations to protect your business from legal and financial risks.

Managed security services
24/7 Security Monitoring:
24/7 security monitoring of your network, systems, and applications. We use advanced SIEM technology to detect threats in real-time.
Threat Detection and Response:
Proactive threat hunting and rapid incident response (MDR) to neutralize cyberattacks before they cause damage.
Vulnerability Management:
Regular vulnerability assessments and penetration testing to identify and remediate security weaknesses.
Security Device Management:
We manage and maintain your firewalls, IDS/IPS, and endpoint security.